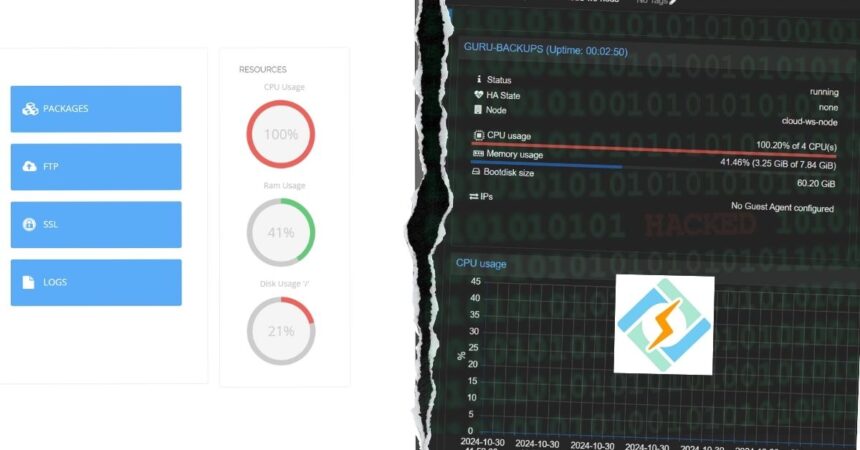
From a routine morning check on server health, I started noticing unusual patterns. Initially, I thought it might be a minor vulnerability affecting one of our nodes, or possibly related to my business partner’s website due to its visibility in the industry.
To be certain, I checked if any login details or IP addresses might have been shared externally. However, upon examining both private and public nodes, I quickly realized that several CyberPanel-based servers across our network were facing SYN flood attacks. This issue was widespread, affecting unrelated nodes and even extending beyond our core network.
The situation escalated on October 29, 2024, when alerts highlighted unusual access patterns. Logs showed significant resource consumption linked to the LiteSpeed Cache plugin on WordPress installations managed through CyberPanel.
Around the same time, reports emerged that over 22,000 CyberPanel servers were exposed to critical vulnerabilities, making them targets for SYN flood and crypto mining malware attacks. Providers like DigitalOcean and Linode were heavily impacted.
CyberPanel’s lead developer, Usman Nasir, responded promptly, urging users to update their systems to address these actively exploited vulnerabilities, particularly those related to RCE (Remote Code Execution) and DDoS attacks.
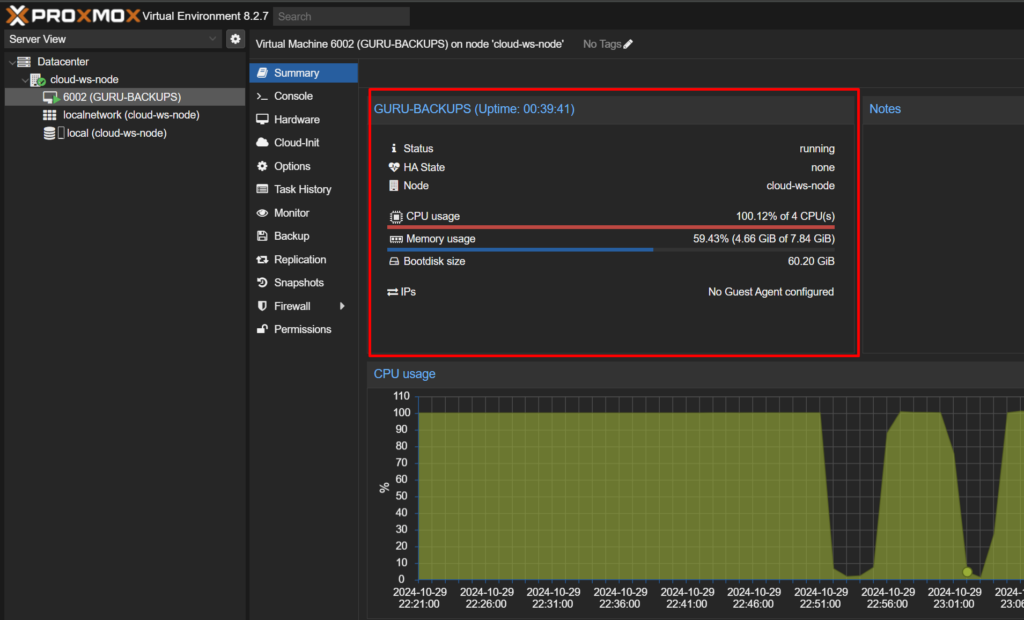
Our clients were hit particularly hard, with some servers experiencing downtime of up to 28 minutes, impacting performance and reliability. This real-world impact underscored the importance of taking immediate action.
Based on my experience with server security and management, I compiled the steps below, drawn directly from what worked for us in identifying and addressing this malware threat. If you have additional insights or suggestions, feel free to contribute in the comments to help others who may encounter similar challenges.
In this article, you’ll learn how to:
- Identify and Analyze Crypto Mining Malware and SYN Flood Attacks on CyberPanel: Learn to detect unusual spikes in CPU usage and identify suspicious processes in your logs that could indicate mining malware or SYN flood activity impacting your server’s resources.
- Inspect Network Traffic for Unauthorized crypto Mining Activity: Discover techniques to monitor network traffic and identify connections to unauthorized mining pools or control servers, helping you pinpoint suspicious IPs that may be exploiting your server.
- Stop and Remove Crypto Mining Malware on CyberPanel Servers: Follow step-by-step instructions to locate and permanently remove crypto mining malware, addressing persistent scripts or files left by mining processes to prevent them from reappearing.
- Update CyberPanel and WordPress to Block Crypto Mining Vulnerabilities: Find out how to secure CyberPanel and related plugins by applying updates that specifically target vulnerabilities commonly exploited in crypto mining attacks.
- Set Up Continuous Monitoring for SYN Flood and Crypto Mining Detection: Implement automated monitoring with custom scripts to detect high resource usage and suspicious network activity, ensuring early alerts and ongoing protection against SYN floods and crypto mining threats.
By following these steps, you’ll be equipped to regain control over your server, prevent further infections, and ensure smooth operation for your applications.
1. Identifying Cyberpanel Crypto Mining Malware and SYN Flood Attacks
Mining malware exploits server resources to mine cryptocurrency, which can lead to high CPU usage and increased network traffic. This type of malware often infiltrates servers through vulnerabilities, using the server’s resources to mine coins while degrading performance. In some cases, mining malware may trigger SYN flood attacks, where the infected server sends a high volume of SYN packets to overwhelm another target.
If your server has been compromised in this way, your logs might show SYN flood activity with your server as the source. Here’s an example of what this could look like, with placeholder IPs for privacy:
Attack detail : 41Kpps/314Mbps
dateTime srcIp:srcPort dstIp:dstPort protocol flags packets bytes reason
2024.10.29 03:55:43 CET YourServerIP:13118 203.0.113.15:25565 TCP SYN 16384 15695872 ATTACK:TCP_SYN
2024.10.29 03:55:43 CET YourServerIP:50958 203.0.113.15:25565 TCP SYN 16384 15695872 ATTACK:TCP_SYN
2024.10.29 03:55:43 CET YourServerIP:35112 203.0.113.15:25565 TCP SYN 16384 15695872 ATTACK:TCP_SYN
In these logs, 202.55.23.105 (the attacker’s IP) is sending SYN packets toward In this case, YourServerIP is the source IP sending SYN packets to 203.0.113.15 on port 25565. Each packet has a SYN flag, meaning the connections remain half-open, which can drain the target server’s resources. Repeated patterns like these suggest that your server may be infected with mining malware, using its power to flood other targets.
Checking CPU and Memory Usage for Mining Malware
To see if mining malware is consuming your server resources, start by checking for high CPU or memory usage. Open the terminal and type:
topFocus on processes with high values in the %CPU and %MEM columns. To get a quick list sorted by CPU usage, use:
ps aux --sort=-%cpu | head -n 10If mining malware is present, you might see suspicious processes, such as [kworker/1:0-events] or kdevtmpfsi, consuming significant CPU resources. Here’s an example:
root@guru:~# ps aux --sort=-%cpu | head -n 10
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 700 108 6.0 2439388 181112 ? Ssl 07:13 4:39 [kworker/1:0-events] -c /usr/.network-setup/config.json
In this example, [kworker/1:0-events] is consuming 108% of CPU and points to the configuration file /usr/.network-setup/config.json, which is unusual for a legitimate process. Another example might show kdevtmpfsi running from /tmp, which is often associated with mining malware:
root@GURU-BACKUPS:~# ps aux --sort=-%cpu | head -n 10
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1514 375 0.0 2879160 6368 ? Ssl 20:03 82:47 /tmp/kdevtmpfsi
Processes like /tmp/kdevtmpfsi using extremely high CPU indicate mining malware that’s consuming resources to mine cryptocurrency.
Investigating Suspicious Processes
To confirm if these suspicious processes are related to mining malware, check their associated configuration files. For a process pointing to /usr/.network-setup/config.json, you can inspect the file by running:
cat /usr/.network-setup/config.json
If this file reveals mining pool URLs, such as pool.hashvault.pro:80, or other settings optimized for high CPU usage, it’s a strong indication of mining malware.
Similarly, inspect /tmp/kdevtmpfsi or any other unfamiliar process by checking the file:
cat /tmp/kdevtmpfsi
If it contains configurations or scripts pointing to mining pools, your server is indeed infected.
Cleaning Up and Securing the Server
To remove the malware, terminate the malicious process with:
kill -9 <PID>
Replace <PID> with the actual process ID, such as 700 for [kworker/1:0-events] or 1514 for kdevtmpfsi. After stopping the process, delete the associated files to ensure it doesn’t restart:
For /usr/.network-setup/, use:
rm -rf /usr/.network-setup/
For kdevtmpfsi, remove it with:
rm -rf /tmp/kdevtmpfsi
Search for additional suspicious files in directories like /tmp/ to ensure no other malware remains:
find /tmp/ -type f -name "kdevtmpfsi"
Why Your IP Might Get Blocked by Hosting Providers Like OVH
If mining malware is using your server to conduct SYN flood attacks, your hosting provider may flag your IP for unusual or suspicious activity. Hosting providers like OVH monitor for patterns like high outbound traffic or repeated SYN packets originating from your IP, which often indicate a compromised server.
When this happens, OVH might notify you via email, using subject lines like “Important information regarding IP-14.67.818.174/28 – Anti-hack” or “Notice: IP Suspended for Suspicious Activity”. This email indicates that OVH has detected unusual traffic patterns or malicious activity originating from your IP and has temporarily restricted access to prevent further misuse.
Receiving this notification is a clear signal that your server may be infected. Common reasons include:
- Mining Malware: The malware consumes CPU to mine cryptocurrency, creating noticeable patterns in traffic or resource usage that trigger alerts.
- SYN Flood Attacks: Mining malware or other malicious scripts can lead your server to initiate SYN flood attacks on other IPs. Hosting providers detect these patterns and may restrict your IP to protect their network.
If you receive such a notification, follow the above steps to inspect and clean your server, checking for abnormal CPU usage and suspicious files. Resolving these issues promptly will help you comply with your hosting provider’s anti-hack policies and prevent future restrictions.
2. Inspect Network Traffic for Unauthorized Mining Activity
After identifying unusual CPU usage, the next step is to inspect network traffic for unauthorized connections. Mining malware often initiates outbound connections to external servers, such as mining pools or control centers, which can be detected by analyzing live traffic. Here, we’ll walk through using tools like netstat, iftop, and tcpdump to spot these connections.
Step 1: Checking Active Network Connections with netstat
To see which connections are currently active, use netstat to identify all established and initiating connections on the server. Run:
netstat -tnp
This command lists all active TCP connections, including the IPs and associated processes. The output might show something like:
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.1.100:80 66.249.77.104:48627 TIME_WAIT -
tcp 0 0 192.168.1.100:8090 105.163.2.135:2048 ESTABLISHED 1040/lscpd (#01)
tcp 0 1 192.168.1.100:45112 92.255.110.4:80 SYN_SENT 1460/kdevtmpfsi
In this example, you see an active outbound connection from your server (192.168.1.100) to 92.255.110.4 on port 80 with the SYN_SENT state. This connection is initiated by the kdevtmpfsi process, which is known to be associated with mining malware.
Step 2: Monitoring Live Network Traffic with iftop
Next, monitor real-time traffic with iftop to get an overview of current data usage and connections. Install it by running:
apt install iftop
Once installed, start iftop on your main network interface (in this example, eth0):
iftop -i eth0
In iftop, you might see connections like the following:
192.168.1.100 => vps35034.vpsville.ru 0b 42b 42b
<= 0b 342b 342b
192.168.1.100 => ec2-54-171-73-194.eu-west 0b 54b 54b
<= 0b 54b 54b
192.168.1.100 => one.one.one.one 284b 1.01Kb 1.01Kb
<= 432b 1.60Kb 1.60Kb
Here, 192.168.1.100 is your server IP, with outbound connections to potentially suspicious IPs like vps35034.vpsville.ru and AWS EC2 instances (ec2-54-171-73-194.eu-west). Any unknown IPs with data transfers could indicate unauthorized mining activity, especially if they are connected to high-traffic destinations.
Step 3: Capturing and Analyzing Traffic with tcpdump
For a closer look, capture traffic using tcpdump on port 80, which is commonly targeted by mining malware. Save the captured traffic to a file for further inspection:
tcpdump -i eth0 port 80 -w suspicious_traffic.pcap
This command captures all traffic on port 80 and saves it to suspicious_traffic.pcap. Once you’ve captured enough data, stop tcpdump by pressing Ctrl+C, then review the file using tcpdump or Wireshark for any unusual IPs.
Step 4: Blocking Suspicious IPs
If you confirm that certain IPs are unauthorized or linked to suspicious activity, block them using UFW to prevent further access. For example, to block 92.255.110.4, run:
sudo ufw deny from 92.255.110.4
If you need to block a range, such as 203.0.113.0/24, use:
sudo ufw deny from 203.0.113.0/24
To confirm that these IPs are blocked, check the firewall status with:
sudo ufw status
Blocking these IPs prevents further unauthorized connections, reducing the risk of external control over your server by mining malware or other malicious actors. By using these tools, you can effectively monitor, capture, and block suspicious network activity to maintain server security.
Step 5: Enabling Server-Side SYN Flood Protections
After blocking suspicious IPs, it’s essential to add further protection against SYN flood attacks by configuring your server to handle higher volumes of connection attempts. By enabling SYN cookies and adjusting TCP settings, you’ll make your server more resilient to these attacks.
To get started, open the sysctl.conf file to add the necessary configurations:
sudo nano /etc/sysctl.conf
Append the following lines at the end of the file to activate SYN cookies, reduce retry attempts, and expand the backlog for half-open connections:
net.ipv4.tcp_syncookies=1
net.ipv4.tcp_syn_retries=2
net.ipv4.tcp_max_syn_backlog=4096
net.ipv4.tcp_syncookies=1enables SYN cookies to handle high volumes of half-open connections, which mitigates SYN flood effects.net.ipv4.tcp_syn_retries=2reduces retry attempts for SYN-ACK responses, helping prevent overloads from unreachable clients.net.ipv4.tcp_max_syn_backlog=4096increases the backlog queue for half-open connections, allowing your server to handle more incoming requests.
After editing, apply the changes immediately by running:
sudo sysctl -p
Note: Enabling SYN cookies may occasionally interfere with ad tracking services, such as Google AdSense, which can impact analytics or reported impressions. Monitor your analytics closely after making these changes, and consult your ad provider if you notice discrepancies.
3. Update CyberPanel and LiteSpeed Cache Plugin to Block Crypto Mining Vulnerabilities
Securing CyberPanel and related WordPress plugins, such as LiteSpeed Cache, is essential after addressing malware. Regular updates, careful inspection, and enhanced security practices help prevent future vulnerabilities.
Start by updating CyberPanel to make sure all known security patches are applied. Use this command:
sh <(curl https://raw.githubusercontent.com/usmannasir/cyberpanel/stable/preUpgrade.sh || wget -O - https://raw.githubusercontent.com/usmannasir/cyberpanel/stable/preUpgrade.sh)
This command ensures CyberPanel is up-to-date, closing any vulnerabilities that attackers could exploit.
Update the LiteSpeed Cache Plugin to version 6.5.1 or later. This update addresses a critical stored XSS vulnerability (CVE-2024-47374) that allowed unauthenticated users to execute arbitrary JavaScript, which could lead to privilege escalation. This issue affected over 22,000 servers and highlights the importance of timely plugin updates.
Keep Your WordPress and Plugins Secure
- Update WordPress Core: Go to Dashboard > Updates in your WordPress admin panel and click Update Now.
- Update the LiteSpeed Cache Plugin: Navigate to Plugins > Installed Plugins, and update LiteSpeed Cache to at least version 6.5.1.
- Update All Plugins: Select and update all active plugins to ensure they’re not vulnerable.
To restrict PHP execution within the uploads directory, add an .htaccess file in /wp-content/uploads with the following content:
<FilesMatch "\.(php|phtml|php3|php4|php5|php7|phar)$">
Deny from all
</FilesMatch>
This rule stops PHP files from running in the uploads directory, reducing the risk of hidden malware backdoors.
Set secure file permissions to limit unauthorized modifications. Run:
chmod -R 755 /path/to/wp-content
chown -R www-data:www-data /path/to/wp-content/uploads
These commands restrict write access to the necessary files, enhancing directory security.
Disabling file editing within the WordPress dashboard prevents attackers from modifying files directly if they gain admin access. To disable this feature, add the following lines to wp-config.php:
define('DISALLOW_FILE_EDIT', true);
define('DISALLOW_FILE_MODS', true);
Next, check for recently modified files within your WordPress directory, which can reveal hidden changes made by unauthorized users. Run:
find /path/to/wordpress -type f -mtime -7
Review the results, focusing on unexpected changes within /wp-content/plugins and /wp-content/themes.
To identify potentially harmful files, search for PHP files in the uploads directory. Run:
find /path/to/wordpress/wp-content/uploads/ -name "*.php"
Open any unexpected PHP files and examine them to confirm they’re not malicious.
Search for obfuscated functions commonly used in backdoors, such as eval(base64_decode(...)), exec(), or shell_exec(). Run:
grep -rE 'eval\(base64_decode|exec|shell_exec|passthru|system' /path/to/wordpress
This command will locate files containing these potentially harmful functions, helping you detect hidden malware.
Review key configuration files such as wp-config.php and .htaccess for unauthorized modifications. Open these files and inspect for any unfamiliar code:
nano /path/to/wordpress/wp-config.php
nano /path/to/wordpress/.htaccess
Check cron jobs to ensure no unauthorized entries persist. Malware often uses cron jobs to restart itself. List cron jobs for both root and the web server user:
crontab -l
crontab -u www-data -l
Remove any suspicious entries, especially those that reference unexpected scripts or paths.
Finally, ensure WordPress core and plugins are regularly updated. You can update WordPress core files from the Dashboard > Updates section, or use WP-CLI by running:
wp core update
Also, update plugins under Plugins > Installed Plugins, paying close attention to security-critical plugins.
4. Set Up a Continuous Monitoring Tool On Cyberpanel
Maintaining server security over time requires consistent monitoring and preventive measures to address potential threats as they arise. This section provides practical steps to secure your server with Cloudflare protection, continuous monitoring through a custom script, and enhanced WordPress security to safeguard against vulnerabilities.
Protecting Your Server with Cloudflare
Cloudflare can act as a first line of defense by filtering incoming traffic, protecting against DDoS attacks, and blocking bots before they reach your server. To get started, sign up on Cloudflare’s website and add your domain. Set up your DNS to route through Cloudflare, and in your Cloudflare settings, enable Bot Fight Mode and set the security level to High. This configuration helps prevent suspicious traffic, such as bots and brute-force login attempts, from reaching your server.
Using Cloudflare is especially helpful if you notice repeated login attempts or spikes in traffic from unknown sources. By filtering this traffic, Cloudflare reduces the workload on your server and helps block potentially harmful requests.
Continuous Monitoring with Netdata or Monit for Threat Detection
Alongside Cloudflare, a reliable monitoring tool like Netdata or Monit provides continuous visibility over your server’s performance, helping detect potential attacks or unusual resource spikes, such as those from SYN flood attempts or crypto mining activity. Each tool offers distinct advantages, letting you choose the best fit for your server setup.
Option 1: Netdata for Detailed Real-Time Monitoring
Netdata is ideal for users who want a visual, interactive dashboard for tracking CPU, memory, disk, and network usage. This tool provides a live view of your server’s metrics, making it easy to spot unusual activity at a glance.
To install Netdata, use:
bash <(curl -Ss https://my-netdata.io/kickstart.sh)
Start Netdata with:
sudo systemctl start netdata
Access the dashboard at http://<your-server-ip>:19999 for real-time insights into your server’s activity.
Option 2: Monit for Lightweight Core Monitoring
Monit is suited for those seeking a simpler solution with minimal resource impact. It monitors essential metrics like CPU and memory and sends quick alerts if thresholds are exceeded, making it a reliable choice for servers needing efficient monitoring.
To install Monit, run:
sudo apt update && sudo apt install monit -y
Enable and start Monit:
sudo systemctl enable monit
sudo systemctl start monit
Configure Monit to trigger alerts by editing the configuration file /etc/monit/monitrc. For example, to set alerts for memory usage over 75% and a load average above 4, add:
check system $HOST
if loadavg (1min) > 4 then alert
if memory usage > 75% then alert
Restart Monit to apply changes:
sudo systemctl restart monit
Choosing between Netdata and Monit allows you to match the monitoring tool with your server’s requirements, balancing detailed metrics with efficiency. Integrating either option with Cloudflare’s filtering adds a robust layer of security and detection, reducing threats and ensuring a stable CyberPanel environment.
Frequently Asked Questions (FAQs)
Based on questions from clients and others affected by recent CyberPanel attacks, I’ve put together answers to common concerns, using both the information covered above and my hands-on experience. These FAQs should help clarify what to expect from SYN flood attacks and mining malware, and provide guidance on applying the solutions we’ve discussed effectively.
1. Is this type of attack preventable, or is it just a matter of time before it happens?
While no system is entirely immune, enabling SYN flood protections, monitoring network traffic, and keeping software updated significantly lowers the risk. Implementing these measures makes your server a much harder target, which can deter many automated attacks. Regular maintenance and monitoring are essential to stay ahead of evolving threats.
2. Can I fix this issue myself, or will I need expert help?
You can certainly address these issues yourself using the steps outlined in this guide. Many admins have successfully stopped similar attacks by following these steps, especially if the attack is limited to SYN floods or resource-hogging malware. However, if the attack continues or you’re unfamiliar with network security, consulting a cybersecurity expert may be wise for a more in-depth assessment.
3. How do I know if my CyberPanel server is already compromised?
Signs of compromise include unusual CPU spikes, unexpected processes, or unauthorized connections. Check your resource usage in CyberPanel and look for suspicious processes. Running commands like ps aux --sort=-%cpu helps you identify high CPU consumers that might indicate mining malware.
4. Are these solutions enough to protect my server long-term?
These measures address the immediate threats posed by SYN floods and mining malware. For ongoing protection, combine these steps with a routine of updating software, restricting unnecessary access, and implementing additional layers like a web application firewall (WAF). Security is an ongoing process rather than a one-time setup.
5. Will enabling SYN cookies or Cloudflare protection affect my legitimate traffic or analytics?
Yes, enabling SYN cookies and Cloudflare can sometimes impact analytics, especially with tracking services like Google AdSense. SYN cookies, in particular, may interfere with ad impressions and analytics reporting, as they alter the way connections are handled. Monitor your analytics after enabling these protections, and if necessary, adjust settings to balance security with ad tracking.
6. How quickly should I expect results after implementing these changes?
You should notice reduced CPU usage and fewer connection spikes almost immediately after applying SYN flood protections and removing any detected malware. However, for ongoing improvement, continue monitoring your server to verify that no new attacks or malware reappear over time.
7. What should I do if I notice high CPU usage again after some time?
High CPU usage could indicate new attacks or residual malware. Check active processes regularly and monitor logs for unusual connections. If the issue persists, you may need to re-evaluate firewall settings, network traffic, and possibly seek assistance for a deeper analysis of server logs.
8. Can I still get flagged by my hosting provider even after these steps?
Yes, hosting providers like OVH or DigitalOcean monitor for high outbound traffic or suspicious activity. Implementing these protections greatly reduces the chance of being flagged, but consistent monitoring and immediate action upon noticing irregularities are key to avoiding provider restrictions.
9. How does Cloudflare help, and will it completely stop these attacks?
Cloudflare acts as an extra layer of security by filtering incoming traffic, blocking bots, and mitigating DDoS attacks before they reach your server. While it’s highly effective for SYN flood and DDoS protection, it’s not foolproof and should be part of a layered approach, including strong server-side defenses.
10. How do I know if the measures I’ve implemented are working?
Monitor CPU and network traffic over the next several days after implementing these steps. You should see a noticeable decrease in CPU spikes and fewer suspicious connections. Setting up alerts for unusual CPU or network usage can help confirm that your server remains secure over time.
Conclusion
This guide provides a practical approach to identifying and stopping mining malware and SYN flood attacks on CyberPanel, addressing immediate threats and setting up long-term defenses. By implementing these steps, you gain control over server resource usage, blocking threats before they escalate.
If you have insights or techniques that have worked for you, feel free to share them in the comments. I’ll continue updating this guide based on user feedback and experiences drawn from my own client projects. This ongoing approach helps all of us stay ahead of evolving threats and keeps CyberPanel servers secure.